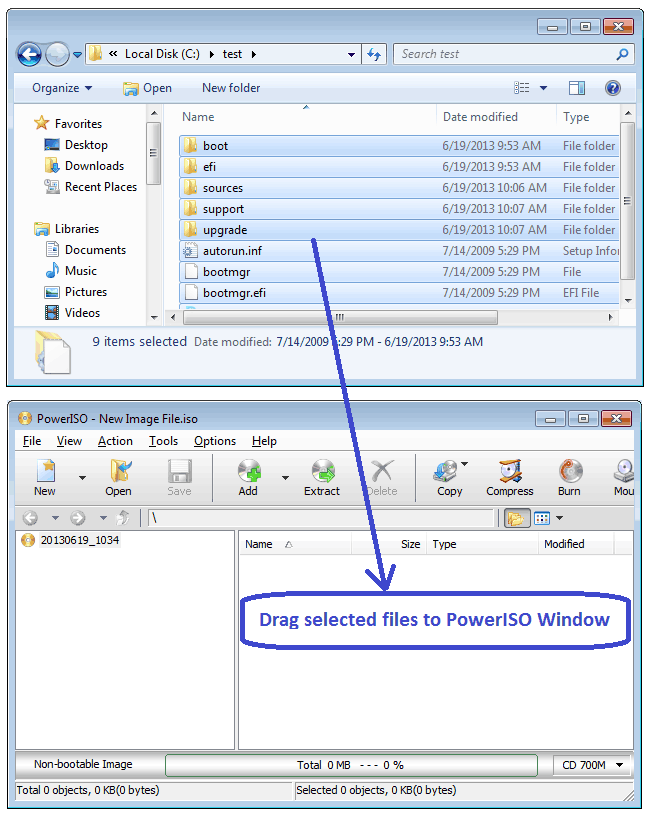
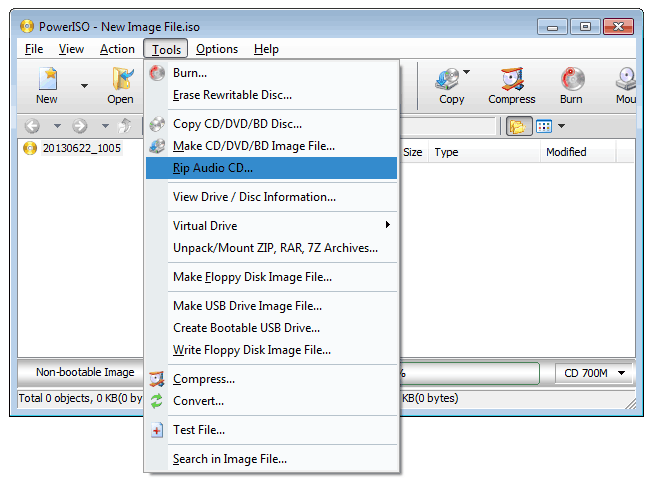
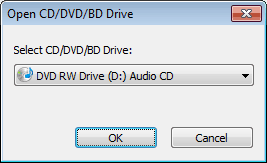
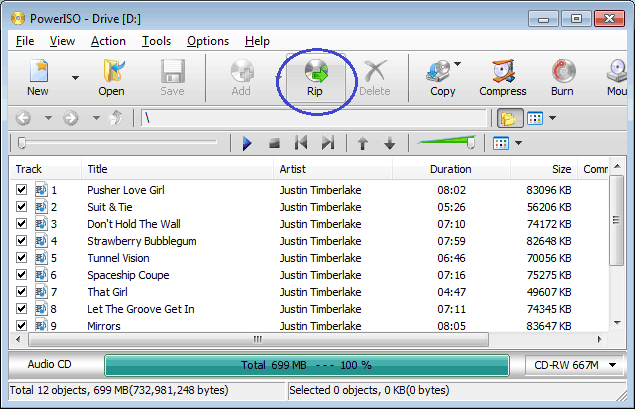
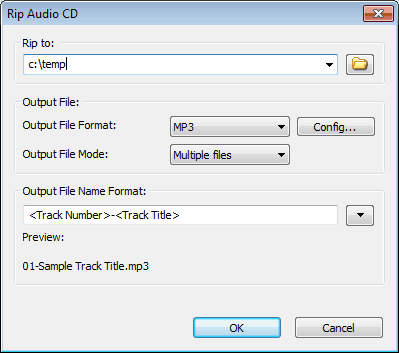
PowerISO can not only copy Audio CD to image file, but also rip it to MP3 files. It can also rip Audio CD to APE, FLAC, WMA, or WAV files.
|
Sunday, August 25, 2013
How to use PowerISO as MP3 Ripper?
How to use PowerISO as ISO Extractor?
You can use PowerISO as ISO extractor in three ways, using the main program, using the shell context menu, or using the drag-and drop.
Usage1: Extractor ISO file using the main program:
- Run PowerISO, click the "Open" button on toolbar or choose "File > Open" menu to open an existing iso file. You can also open the iso file by simply double clicking on it.
- Click the "Extract" button on toolbar. PowerISO shows the iso extractor dialog.
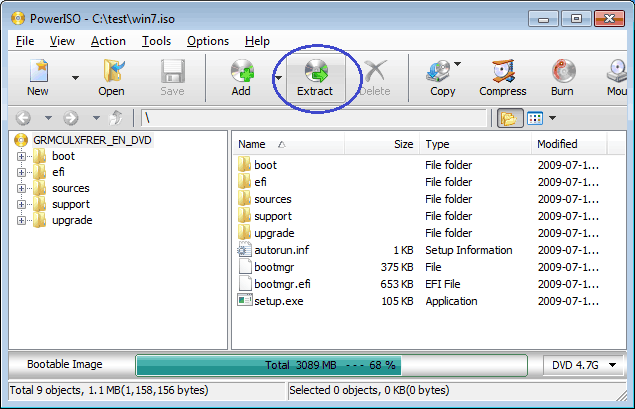
- Choose the destination folder, then click "OK" to start extracting.
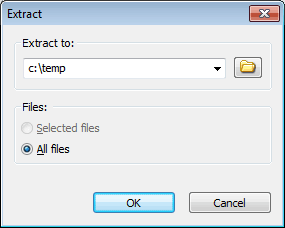
Usage2: Extract ISO file using the shell context menu:
- Open "My Computer" and select the iso file which you want to extract.
- Right-click on the file selected, the shell context menu will popup.
- Choose the menu "Extract here using file names and folders".
- The iso extractor will start to run. It will automatically create a folder using the file name, and extract all files in the iso file to this folder.
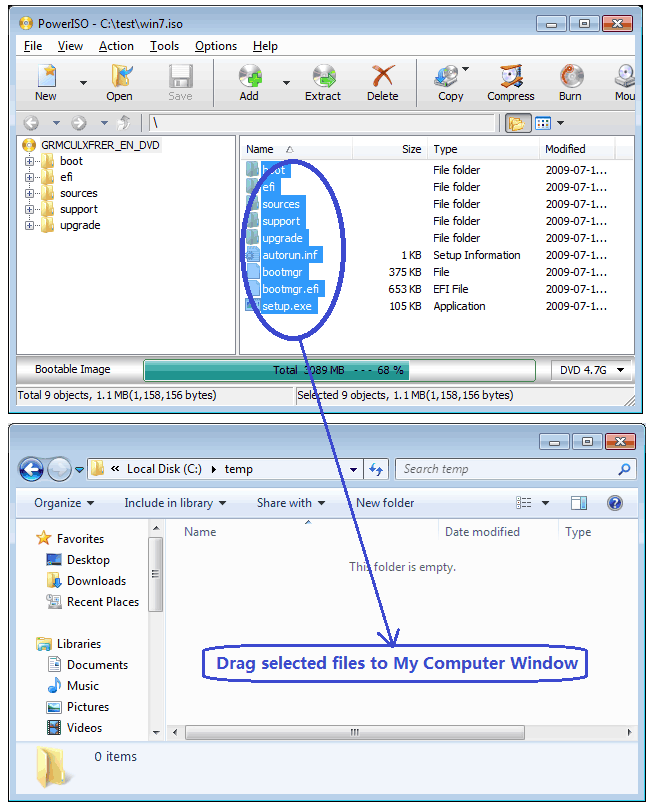
Usage3: Extract ISO file using the drag and drop:
- Run PowerISO, click the "Open" button on toolbar or choose "File > Open" menu to open an existing iso file. You can also open the iso file by simply double clicking on it.
- Open "My Computer".
- Select all files you want to extract, then drag it to "My Computer".
How to use PowerISO as ISO Creator?
PowerISO can create ISO from files and folders in the hard disc. There are three ways to launch the iso creator, using the main program, using the shell context menu, or using the drag-and drop. With PowerISO, You can create ISO file with a single click!
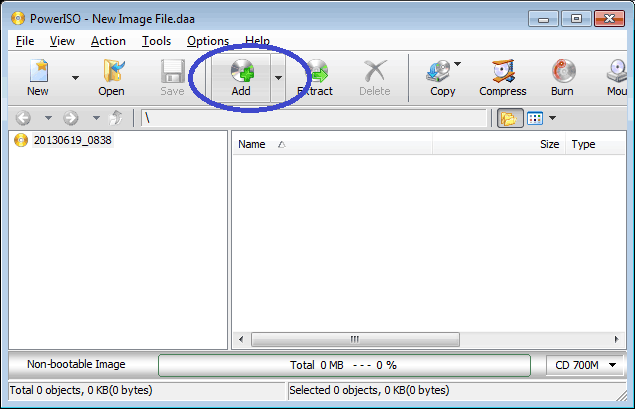
Usage1: Create ISO file using the main program:
- Run PowerISO.
- Click the "Add" button on toolbar to add files and folders. You can also directly drag files and folders from Windows Explorer to PowerISO window.
Another method to add files is using the system clipboard. You can select files and folders in Windows Explorer, hit "CTRL-C" to copy them to clipboard, then go to PowerISO window, and hit "CTRL-V" to paste selected files and folders to current compilation.
- Choose the menu "Action > New Folder" to create a new folder.
- Choose the menu "Action > Change Label" to change the default label.
- Choose the menu "File > Properties" to set the iso file properties.
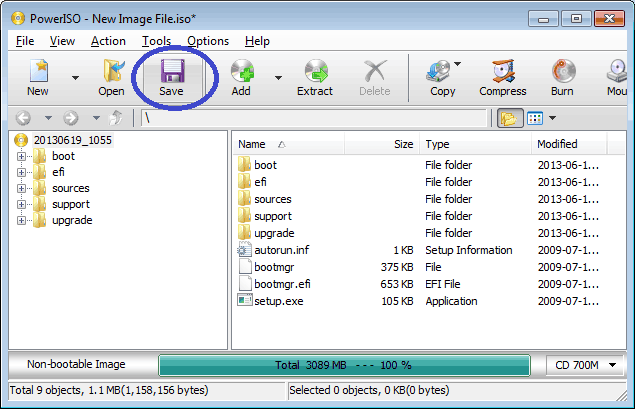
- After you have added all files and folders and made all necessary changes, click the "Save" button on toolbar, or choose the "File > Save" menu to save the iso file.
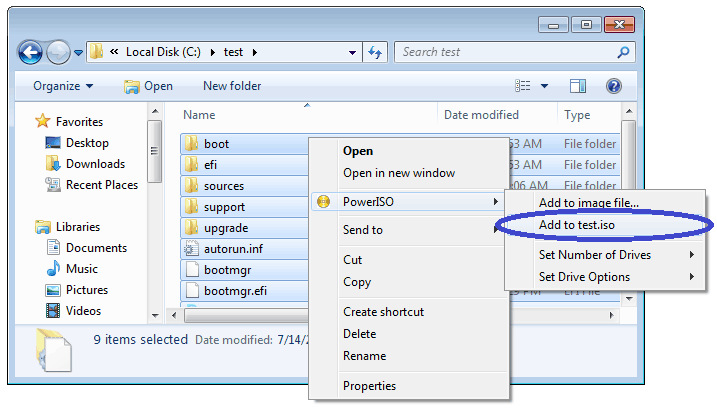
Usage2: Create ISO file using the shell context menu:
- Open "My Computer" and select the files and folders which you want to add to iso file.
- Right-click on the files selected, the shell context menu will popup.
- Choose the menu "Add to xxxxx.iso".
- PowerISO main program will start to run. It will automatically add all files and folders selected to the current compilation, then save the iso file with the specified name.
(Notes: The default image type for saving is DAA, you can change it to ISO format in PowerISO configuration dialog.)
Usage3: Create ISO file using the drag and drop:
- Run PowerISO.
- Open "My Computer" and select the files which you want to add to iso file.
- Drag all files and folders selected to the PowerISO window.
(Notes: You can also add files and folders using system clipboard.)
- Click the "Save" button to save the iso file..
How to use PowerISO as MP3 Burner?
PowerISO can not only create DATA CD / DVD, but also create Audio CD from music files. PowerISO supports almost all music files, including MP3, APE, FLAC, WMA, and WAV files.
- Run PowerISO.
- Choose "File > New > Audio CD Image" Menu.
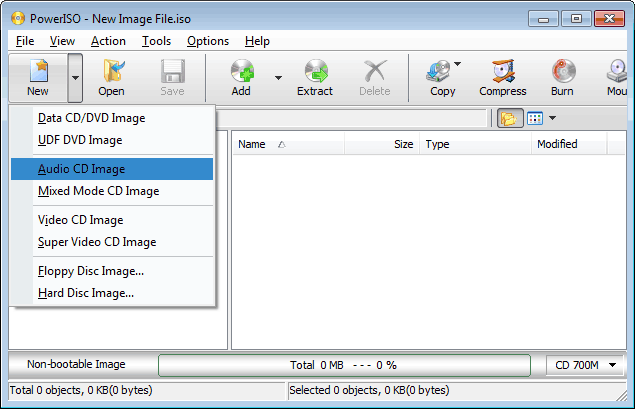
- Click "Add" button on toolbar.
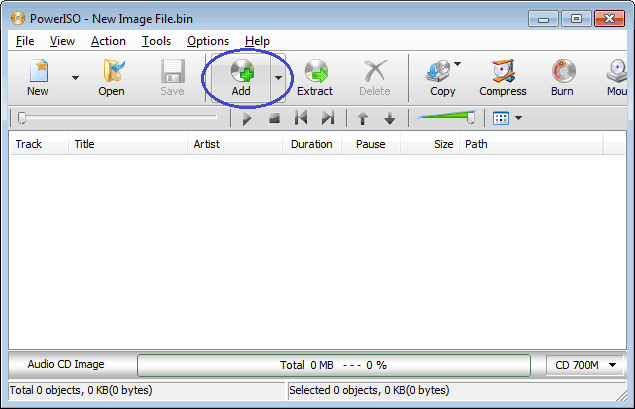
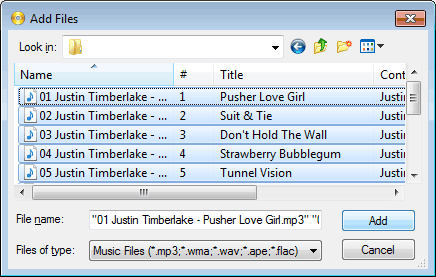
- Select Mp3 files which you want to burn, then click "Add" to add them to the current compilation.
- Click "Burn" button on toolbar.
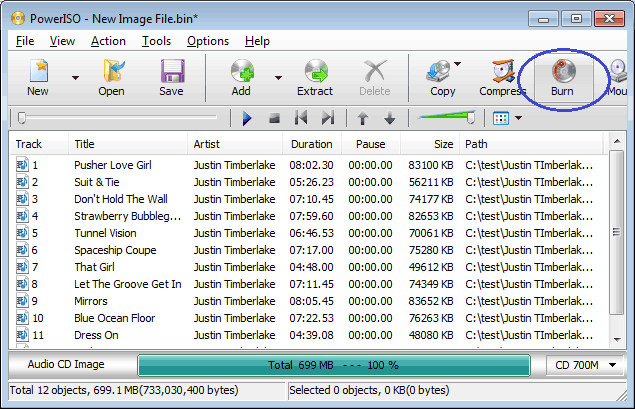
- PowerISO shows Mp3 burner dialog.
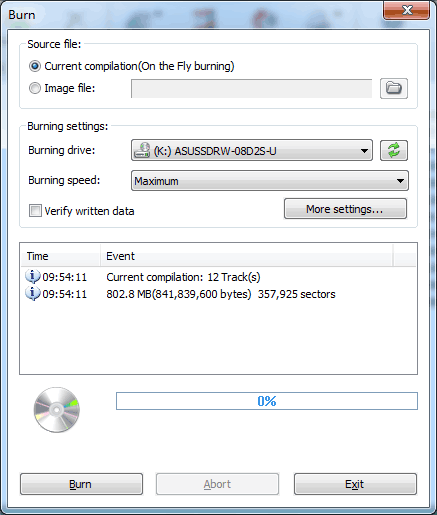
- Choose the burning drive which holds a blank CD-R disc.
- Choose the burning speed.
- Click "Burn" to start burning mp3 files.
How to create Windows 7 installation disc from pre-prepared source directory?
Below is a guide on how to create Windows 7 installation disc from pre-prepared source directory. The source directory should include all files copied from Windows 7 disc, which looks like follows,
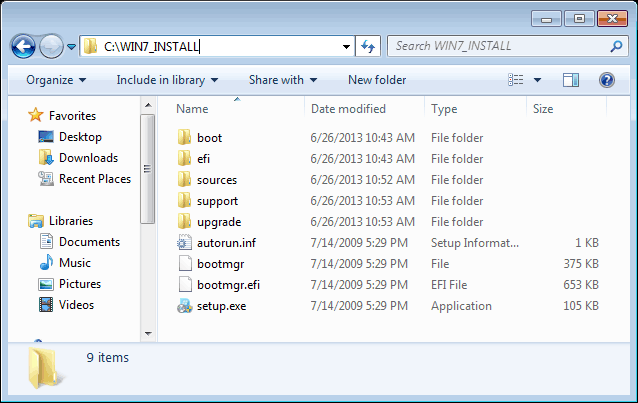
1. Start PowerISO.
2. Click "Add" button to add all files and folders under the source directory to current compilation.
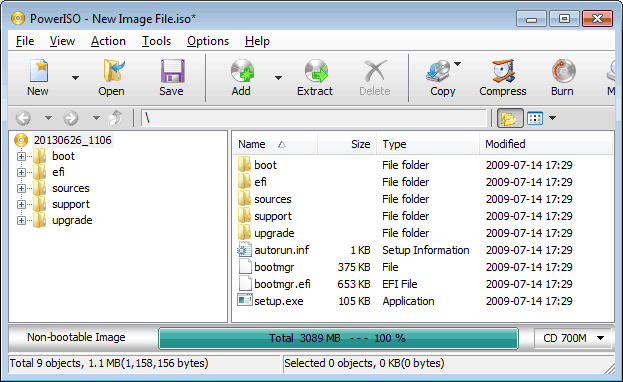
3. Click the menu, "Action --> Boot --> Add Boot Information...", and select etfsboot.com, then click "OK" to add it as boot file. 'etfsboot.com' can be found in the boot folder under the source directory.
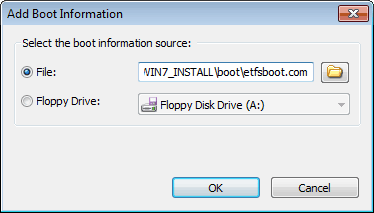
4. Insert a blank DVD disc in the writer, then click "Burn" button on toolbar to burn the current compilation to the disc.
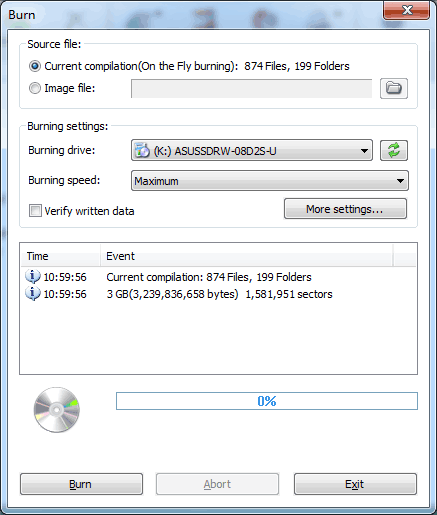
If no errors occurred in the above process, you should now get a new Windows 7 installation disc.
You can also save current compilation to get a bootable ISO file in step 4. You can burn the ISO file later to get the Windows installation disc.
Windows 8 and Windows vista installation can also be created using the similar way.
How to Setup Windows 7 or Windows 8 from USB drive?
Step1: Create Bootable USB Drive:
- Start PowerISO (v4.8 or newer version, download here).
- Insert the USB drive you intend to boot from.
- Choose the menu "Tools > Create Bootable USB Drive". The "Create Bootable USB Drive" dialog will popup. If you are using Windows Vista or Windows 7 / 8 operating system, you need confirm the UAC dialog to continue.
- In "Create Bootable USB Drive" dialog, click "..." button to open the iso file of Windows 7 or Windows 8.
- Select the correct USB drive from the "Destination USB Drive" list if multiple USB drives are connected to the computer.
- Choose the proper writing method. "USB-HDD" is recommended.
- Click "Start" button to start creating windows 7 / 8 bootable USB drive.
If no errors occurred in the above process, you should now be all set to setup Windows 7 / 8 from USB drive!
Step 2: Configuring the BIOS:
You should now reboot and go into the BIOS configuration to boot from USB. Instructions for doing so wildly from system to system, but generally entail the following:
- Reboot the system.
- While booting (before Windows starts loading), get into the BIOS configuration screen by hitting something like F1, F2, Delete or Escape. Hotkey instructions are generally provided on the screen.
- Go to the section that contains your boot devices.
- With your USB drive plugged in, the USB drive should be listed. If it isn’t, your system might not support booting from USB. Assuming that it is supported (as is the case with virtually all modern hardware), promote your USB drive to the primary boot device.
- Exit from the BIOS configuration, saving all changes.
If you’re completely new to BIOS configuration, BIOS for Beginners over at Tom’s Hardware might be a good primer. Be aware though, that you can seriously screw up your system by providing incorrect settings!
Step 3: Booting and setup windows 7 / Windows 8 from USB drive:
Assuming that you properly configured your BIOS and your USB drive supports booting, Windows 7 / 8 setup should now load. Depending on the speed of your USB drive, this may take a while.
If it isn’t working, then double-check the following before making a scene:
- Is your BIOS properly configured for booting from the USB device? (Is the USB device listed and does it have top priority?)
- Have you correctly prepared the USB drive in step one? (Restart the procedure.)
- Does your USB drive properly support being booted from? (Try another one!)
How to Setup Windows XP from USB drive?
Step1: Prepping BartPE:
First we’ll prep the USB drive we’ll be using for booting. This is by far the largest step in the process, though it shouldn’t be difficult for anyone to follow. It requires a functional Windows system.
Step2: Create XP Bootable USB Drive:
If no errors occurred in the above process, you should now be all set to setup Windows xp from USB drive!
Step 3: Configuring the BIOS:
You should now reboot and go into the BIOS configuration to boot from USB. Instructions for doing so wildly from system to system, but generally entail the following:
If you’re completely new to BIOS configuration, BIOS for Beginners over at Tom’s Hardware might be a good primer. Be aware though, that you can seriously screw up your system by providing incorrect settings!
Step 4: Booting into BartPE:
Assuming that you properly configured your BIOS and your USB drive supports booting, BartPE should now load. Depending on the speed of your USB drive, this may take a while.
If it isn’t working, then double-check the following before making a scene:
Step 5: Prepping the Hard Disk:
You need to make sure that your hard drive is partitioned and formatted properly. Especially if you've had Linux or some other operating system on it, you'll need to repartition and format it. BartPE contains DiskPart for disk partitioning and A43 File Manager to format your drive.
If you are sure that your hard drive is set up properly (i.e. it has only run Windows, it contains a valid FAT or NTFS partition) then you can safe yourself the hassle and skip this step.
To repartition (This procedure will destroy any data on the hard drive):
To format (This procedure will destroy any data on the hard drive):
Step 6: Launching Windows XP Setup from USB drive:
With your drive all ready, you can now launch the Windows XP setup with a few custom parameters. Let's assume that the files are available at X:\i386.
Plugging in a device now won’t work. Remember that all USB devices will need to be plugged in right from the start while using BartPE.
Run the following command:
The setup program will then silently close, which might make you think that something went wrong. Don't worry though.
Step 7: Continue Windows XP Setup from Hard disk:
|
Saturday, August 24, 2013
How to use PowerISO as ISO Burner?
PowerISO has a built-in CD / DVD burning engine. You can use
PowerISO as an ISO burner. It can not only burn iso images, but also burn
other image files. You do not need install any other burning software.
-
Run PowerISO, click the "Open" button on toolbar or choose "File > Open" menu to open an existing iso file. You can also open the iso file by simply double clicking on it.
-
Click the "Burn" button on toolbar. PowerISO shows the iso burner dialog.
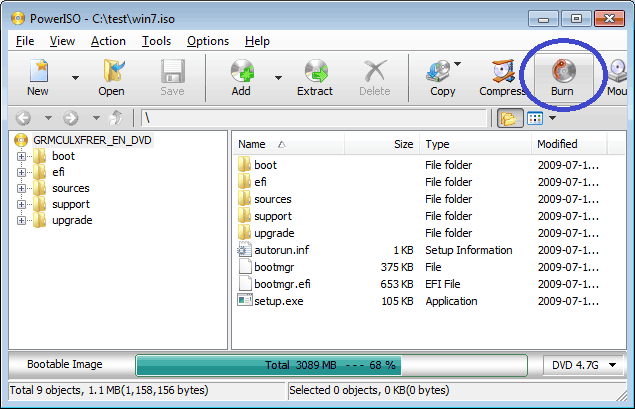
-
Choose the burning drive which holds the disc you want to burn.
-
Choose the burning speed. The default burning speed is the maximum speed supported by the drive and the media.
-
Check the option "Verify written data" to verify the data after burning.
-
Click "Burn" button to start burning iso file.
Make Bootable CD / DVD Disc
-
Run PowerISO.
-
Click on the "New" button on toolbar or choose the "File > New > Data CD / DVD Image" menu.
-
Click on the "Add" button on toolbar to add files and folders. You can also directly drag files and folders from Windows Explorer to the PowerISO window.
-
Choose the menu "Action > New Folder" to create a new folder.
-
Choose the menu "Action > Change Label" to change the default label.
-
Choose the menu "File > Properties" to set the iso file properties.
-
Click on the "Save" button on toolbar, or click on the "File > Save As..." menu.
-
Choose the menu "Action > Boot > Add Boot Information" to load a bootable image file.
-
Save the iso file to "Standard ISO Images (*.iso)" format.
-
To make bootable CD, please burn the iso file to a blank CD / DVD disc.
Saturday, August 17, 2013
How to Merge Two Photos Together With Photoshop
Steps
- 1Select the images for your composition.
- 2Open a new Photoshop document and assign the desired dimensions. For this tutorial, create a document 35x20cm in size using 72dpi (Or whatever the best size for your images) with a white background.
- 3Import the photos to the new document. By doing this you will get 3 different levels: one for the background and one for each image. If you want to reduce or to increase the dimension of one of the images, you can select the level of the chosen image and pressCommand+T (Ctrl+T for Windows) to Free Transform.
- 4Once the dimensions are set up, you have to cancel the image part you don't need. In order to do this select the Eraser tool from the Tool Box and set up the size to 145px and the Hardiness to 15%. Set the Opacity to 30% so the Eraser tool will be less effective and easier to use.
- To be sure to correctly cancel the parts, you can also set up the level in mode toMultiply. This way the level becomes semi-transparent and allows you to see what you have done in the level behind.
- To be sure to correctly cancel the parts, you can also set up the level in mode toMultiply. This way the level becomes semi-transparent and allows you to see what you have done in the level behind.
- 5Once you have done that you can now cancel the parts that are unnecessary.
- 6Control the result of your operation by bringing back the level to Normal mode. To cancel the parts near the merging area of images, modify the settings of the Eraser tool to 30px for size, 100% for opacity, and 40% for hardness.
- 7Select the Brush tool from the tool box, set up the size to 100px, hardness 20% and opacity to 30% using color which best matches with your images. Working with these settings will be simpler to fix the job. With this paint-brush selected we are going to fill the part of the left background with matching color to give it more neat finish.
- 8To work in smaller areas, you should reduce the size of the brush. Just right click with the mouse and choose a smaller size. Once you have removed the area around the bars, you’ll get this result:
Excel - How to Merge cells
Excel - How to Merge cells
This document explains how to merge cells within all versions of Microsoft Excel.
Merging cells is often used when a title is to be centered over a particular section of a spreadsheet. When a group of cells is merged, only the text in the upper-leftmost box is preserved.
To merge a group of cells:
- Highlight or select a range of cells.
- Right-click on the highlighted cells and select Format Cells....
- Click the Alignment tab and place a checkmark in the checkbox labeled Merge cells.
- Highlight or select a range of cells.
- Click the Merge and Center button on the toolbar.Excel XP and Excel 2003

Excel 2007
Excel 2010
How to Merge Multiple PDF Files
How to Merge Multiple PDF Files Into One PDF
These instructions are for merging multiple PDF files into one larger PDF file. Please note that you must have Adobe Acrobat (Standard or Professional), for editing PDF files, installed on your computer. This program is not the same as Adobe Acrobat Reader (which is only able to read/view PDFs).- Run the Adobe Acrobat Standard program (not to be confused with Acrobat Reader) and click "Create PDF" from the toolbar on the main screen.
NOTE: If this toolbar is not visible, then from the menu bar click "View" -> "Task Buttons" -> "Show All Task Buttons". The toolbar should pop up and you can go ahead with Step 1 above. 
- A window will pop up with several parts. Under the "Add Files" area, click Browse to locate and add .pdf files to this compilation. You can add them in any order, or you can add them in the order you want them merged.

- Once you are finished adding the .pdf files, you can move them up/down on the list of .pdf files until that list represents the order which you want the files merged together (from top to bottom).
- When you are done, click "Ok" and the files will be merged.
- A new, merged, .pdf file is created (the one you are viewing), so you need to save this file someplace on your hard drive by clicking "File" -> "Save As..." and saving the new file (with a new name which you must specify) some place on your computer.
Thursday, August 15, 2013
Airborne Internet
Definition of Airborne Internet
There's a new type of service being developed that will take broadband into the air. The airborne Internet won't be completely wireless . There will be ground-based components to any type of airborne Internet network. The consumers will have to install an antenna on their home or business in order to receive signals from the network hub overhead. The networks will also work with established Internet Service Providers (ISPs), who will provide their high-capacity terminals for use by the network. These ISPs have a fiber point of presence their fiber optics are already set up. What the airborne Internet will do is provide an infrastructure that can reach areas that don't have broadband cables and wires
Introduction of Airborne Internet
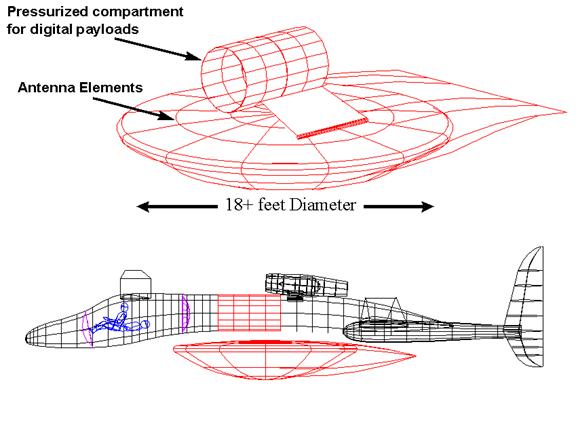
The HALOT Aircraft is under development and flight testing is expected to occur by mid-1998. The aircraft has been specially designed for the HALOT Network with the Communications Payload Pod suspended from the underbelly of its fuselage
The HALOT Aircraft will fly above the metropolitan center in a circular orbit of five to eight nautical miles diameter. The Communications Payload Pod is mounted to a pylon under the fuselage. As the aircraft varies its roll angle to fly in the circular orbit, the Communications Payload Pod will pivot on the pylon to remain level with the ground
The HALOT Network will use an array of narrow beam antennas on the HALOT Aircraft to form multiple cells on the ground. Each cell covers a small geographic area, e.g., 4 to 8 square miles. The wide bandwidths and narrow beamwidths within each beam or cell are achieved by using MMW frequencies. Small aperture antennas can be used to achieve small cells. One hundred dish antennas can be easily carried by the HALOT Aircraft to create one hundred or more cells throughout the service area. If lensed antennas are utilized, wider beams can be created by combining beams through each lens aperture, and with multiple feeds behind each lens multiple beams can be formed by each compound lens.
If 850 MHz of spectrum is assumed, then a minimum capacity of one full-duplex OC-1 (51.84 Mbps) channel is available per cell. For example, a single platform reusing 850 MHz of spectrum in 100 cells would provide the equivalent of two, OC-48 fiber optic rings. The elements in the communications payload are shown below. It consists of MMW transceivers, pilot tone transmitter, high-speed modems, SONET multiplexers, packet switch hardware and software, and associated ancillary hardware such as power supplies, processors, etc
The HALOT Aircraft will fly above the metropolitan center in a circular orbit of five to eight nautical miles diameter. The Communications Payload Pod is mounted to a pylon under the fuselage. As the aircraft varies its roll angle to fly in the circular orbit, the Communications Payload Pod will pivot on the pylon to remain level with the ground
The HALOT Network will use an array of narrow beam antennas on the HALOT Aircraft to form multiple cells on the ground. Each cell covers a small geographic area, e.g., 4 to 8 square miles. The wide bandwidths and narrow beamwidths within each beam or cell are achieved by using MMW frequencies. Small aperture antennas can be used to achieve small cells. One hundred dish antennas can be easily carried by the HALOT Aircraft to create one hundred or more cells throughout the service area. If lensed antennas are utilized, wider beams can be created by combining beams through each lens aperture, and with multiple feeds behind each lens multiple beams can be formed by each compound lens.
If 850 MHz of spectrum is assumed, then a minimum capacity of one full-duplex OC-1 (51.84 Mbps) channel is available per cell. For example, a single platform reusing 850 MHz of spectrum in 100 cells would provide the equivalent of two, OC-48 fiber optic rings. The elements in the communications payload are shown below. It consists of MMW transceivers, pilot tone transmitter, high-speed modems, SONET multiplexers, packet switch hardware and software, and associated ancillary hardware such as power supplies, processors, etc
Summary
Several companies have already shown that satellite Internet access can work. The airborne Internet will function much like satellite-based Internet access, but without the time delay. Bandwidth of satellite and airborne Internet access are typically the same, but it will take less time for the airborne Internet to relay data because it is not as high up. Satellites orbit at several hundreds of miles above Earth. The airborne-Internet aircraft will circle overhead at an altitude of 52,000 to 69,000 feet (15,849 to 21,031 meters). At this altitude, the aircraft will be undisturbed by inclement weather and flying well above commercial air traffic.
Networks using high-altitude aircraft will also have a cost advantage over satellites because the aircraft can be deployed easily -- they don't have to be launched into space. However, the airborne Internet will actually be used to compliment the satellite and ground-based networks, not replace them. These airborne networks will overcome the last-mile barriers facing conventional Internet access optionsThe HALOT Network is capable of providing high rate communications to users of multimedia and broadband services. The feasibility of this approach is reasonably assured due to the convergence of technological advancements. The key enabling technologies at hand include:
Networks using high-altitude aircraft will also have a cost advantage over satellites because the aircraft can be deployed easily -- they don't have to be launched into space. However, the airborne Internet will actually be used to compliment the satellite and ground-based networks, not replace them. These airborne networks will overcome the last-mile barriers facing conventional Internet access optionsThe HALOT Network is capable of providing high rate communications to users of multimedia and broadband services. The feasibility of this approach is reasonably assured due to the convergence of technological advancements. The key enabling technologies at hand include:
- GaAs RF devices which operate at MMW frequencies
- ATM/SONET Technology and Components
- Digital Signal Processing for Wideband Signals
- Video Compression
- Very Dense Memory Capacity
- Aircraft Technology
Intel Core I7 Processor
Definition of Intel Core I7 Processor
Intel core i7 is a family of three Intel desktop processor, the first processor released using the Intel Nehalem micro architecture and the successor to the Intel Core 2 family. All three models are quad core processors.
A quad core processor consists of four cores. Quad core technology is a type of technology that includes two separate dual-core dies, where dual-core means a CPU that includes two complete execution cores per physical processor, installed together in one CPU package. In this setup cores 1 and 2 would share a memory cache, and core 3 and 4 another cache. Communication between core 1 and 2 and core 3 and 4 using QPI(Quick Path Interconnect)
They are 64 bit processors. In computer architecture, 64-bit integers, memory addresses, or other data units are those that are at most 64 bits (8 octets) wide. Also, 64-bit CPU and ALU architectures are those that are based on registers, address buses, or data buses of that size.
The need for core i7 processors requires a comparison with their immediate predecessors. The comparison can be summarized as follows. The Core i7 is a completely new architecture which is much faster and more efficient than the Core 2 Duo. Currently only the Core i7 920, 945 and 965 XE versions are available. Of that the Core i7 920 is available at just $284 which makes it a great buy. It offers better performance than almost all Core 2 Duo processors
A quad core processor consists of four cores. Quad core technology is a type of technology that includes two separate dual-core dies, where dual-core means a CPU that includes two complete execution cores per physical processor, installed together in one CPU package. In this setup cores 1 and 2 would share a memory cache, and core 3 and 4 another cache. Communication between core 1 and 2 and core 3 and 4 using QPI(Quick Path Interconnect)
They are 64 bit processors. In computer architecture, 64-bit integers, memory addresses, or other data units are those that are at most 64 bits (8 octets) wide. Also, 64-bit CPU and ALU architectures are those that are based on registers, address buses, or data buses of that size.
The need for core i7 processors requires a comparison with their immediate predecessors. The comparison can be summarized as follows. The Core i7 is a completely new architecture which is much faster and more efficient than the Core 2 Duo. Currently only the Core i7 920, 945 and 965 XE versions are available. Of that the Core i7 920 is available at just $284 which makes it a great buy. It offers better performance than almost all Core 2 Duo processors
Introduction of Intel Core I7 Processor
A cpu socket or cpu slot is an electrical component that attaches to a circuit board and is designed to house a cpu. It is a special type of IC socket designed for very high pin counts. A cpu socket provides many functions including providing a physical structure to support the cpu, facilitating replacement and cost reduction and as an electrical interface both with the cpu and the circuit board.
Core i7 uses an LGA1366 socket.(socket B). it is incompatible with the previous versions. LGA refers to Land Grid Array and is used as a physical interface for microprocessors of the Intel Pentium 4, Intel Xeon, Intel Core 2 and AMD Opteron families. Earlier the socket used was the PGA(Pin Grid Array). In LGA there are no pins on the chip .Instead there are pads of gold plated copper that touch pins on the motherboard. LGA provides a larger contact point, allowing for eg higher clock frequencies. It also allows higher pin densities and thus enables a more stable power supply to the chip
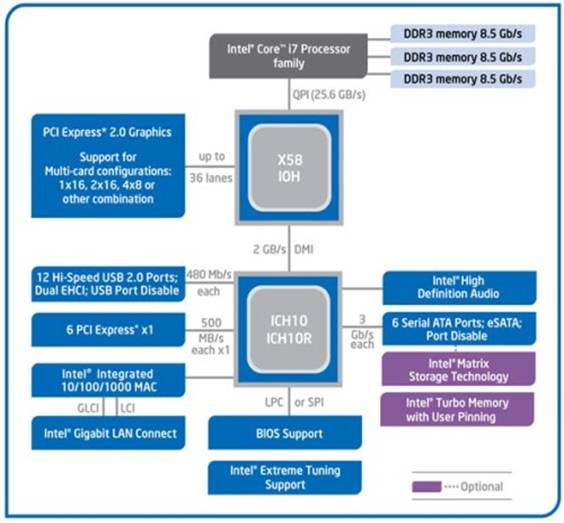 The memory is directly connected to the processor. The memory is divided into three channels. Each channel can support one or two DDR3 RAMs. Motherboards for core i7 have three or six RAM slots.DDR3 RAM is double data rate 3 random access memory. This is a RAM technology used for high speed storage of the working data of a computer or other digital electronic devices. The primary benefit of DDR3 is its ability to run its I/O bus at four times the speed of the memory cells contained in it. It enables faster bus speeds and higher throughputs than earlier memory technologies. There is a significant reduction in the power consumption. It needs only 1.5V compared to 1.8V for DDR2
The memory is directly connected to the processor. The memory is divided into three channels. Each channel can support one or two DDR3 RAMs. Motherboards for core i7 have three or six RAM slots.DDR3 RAM is double data rate 3 random access memory. This is a RAM technology used for high speed storage of the working data of a computer or other digital electronic devices. The primary benefit of DDR3 is its ability to run its I/O bus at four times the speed of the memory cells contained in it. It enables faster bus speeds and higher throughputs than earlier memory technologies. There is a significant reduction in the power consumption. It needs only 1.5V compared to 1.8V for DDR2
Core i7 uses an LGA1366 socket.(socket B). it is incompatible with the previous versions. LGA refers to Land Grid Array and is used as a physical interface for microprocessors of the Intel Pentium 4, Intel Xeon, Intel Core 2 and AMD Opteron families. Earlier the socket used was the PGA(Pin Grid Array). In LGA there are no pins on the chip .Instead there are pads of gold plated copper that touch pins on the motherboard. LGA provides a larger contact point, allowing for eg higher clock frequencies. It also allows higher pin densities and thus enables a more stable power supply to the chip

HOW IT WORKS:
The instruction decoder has three decoder units that can decode one simple instruction per cycle per unit. The other decoder unit can decode one instruction every cycle, either simple instruction or complex instruction made up of several micro-ops.Instructions made up of more than four micro-ops are delivered from the MSROM. Upto four micro-ops can be delivered each cycle to the instruction decoder queue (IDQ).The IDQ delivers micro-op stream to the allocation/renaming stage of the pipeline.
The out-of-order engine supports up to 128 micro-ops in flight. Each micro-ops must be allocated with the following resources: an entry in the re-order buffer (ROB), an entry in the reservation station (RS), and a load/store buffer if a memory access is required.The allocator also renames the register file entry of each micro-op in flight. The inputdata associated with a micro-op are generally either read from the ROB or from theretired register file.
The RS dispatch up to six micro-ops in one cycle if the micro-ops are ready to execute. The RS dispatch a micro-op through an issue port to a specific execution cluster, each cluster may contain a collection of integer/FP/SIMD execution units.The result from the execution unit executing a micro-op is written back to the register file, or forwarded through a bypass network to a micro-op in-flight that needs the result. Intel microarchitecture (Nehalem) can support write backthroughput of one register file write per cycle per port. The bypass network consistsof three domains of integer/FP/SIMD. Forwarding the result within the same bypass domain from a producer micro-op to a consumer micro is done efficiently in hardware without delay.
Forwarding the result across different bypass domains may be subject to additional bypass delays. The bypass delays may be visible to software in addition to the latency and throughput characteristics of individual execution units.Intel microarchitecture (Nehalem) contains an instruction cache, a first-level datacache and a second-level unified cache in each core.
Each physical processor may contain several processor cores and a shared collection of subsystems that are referred to as "uncore". Specifically in Intel Core i7 processor, the uncore provides a unified third-level cache shared by all cores in the physical processor, Intel QuickPath Interconnect links and associated logic. The L1 and L2 caches are writeback and non-inclusive.The shared L3 cache is writeback and inclusive, such that a cache line that exists ineither L1 data cache, L1 instruction cache, unified L2 cache also exists in L3. The L3 is designed to use the inclusive nature to minimize snoop traffic between processor cores. The latency of L3 accessmay vary as a function of the frequency ratio between the processor and the uncore sub-system
The out-of-order engine supports up to 128 micro-ops in flight. Each micro-ops must be allocated with the following resources: an entry in the re-order buffer (ROB), an entry in the reservation station (RS), and a load/store buffer if a memory access is required.The allocator also renames the register file entry of each micro-op in flight. The inputdata associated with a micro-op are generally either read from the ROB or from theretired register file.
The RS dispatch up to six micro-ops in one cycle if the micro-ops are ready to execute. The RS dispatch a micro-op through an issue port to a specific execution cluster, each cluster may contain a collection of integer/FP/SIMD execution units.The result from the execution unit executing a micro-op is written back to the register file, or forwarded through a bypass network to a micro-op in-flight that needs the result. Intel microarchitecture (Nehalem) can support write backthroughput of one register file write per cycle per port. The bypass network consistsof three domains of integer/FP/SIMD. Forwarding the result within the same bypass domain from a producer micro-op to a consumer micro is done efficiently in hardware without delay.
Forwarding the result across different bypass domains may be subject to additional bypass delays. The bypass delays may be visible to software in addition to the latency and throughput characteristics of individual execution units.Intel microarchitecture (Nehalem) contains an instruction cache, a first-level datacache and a second-level unified cache in each core.
Each physical processor may contain several processor cores and a shared collection of subsystems that are referred to as "uncore". Specifically in Intel Core i7 processor, the uncore provides a unified third-level cache shared by all cores in the physical processor, Intel QuickPath Interconnect links and associated logic. The L1 and L2 caches are writeback and non-inclusive.The shared L3 cache is writeback and inclusive, such that a cache line that exists ineither L1 data cache, L1 instruction cache, unified L2 cache also exists in L3. The L3 is designed to use the inclusive nature to minimize snoop traffic between processor cores. The latency of L3 accessmay vary as a function of the frequency ratio between the processor and the uncore sub-system
Phishing
Definition
In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details, by masquerading as a trustworthy entity in an electronic attempting to acquire sensitive information such as usernames, passwords and credit card details, by masquerading as a trustworthy entity in an electronic communication. Phishing is a fraudulent e-mail that attempts to get you to divulge personal data that can then be used for illegitimate purposes.
There are many variations on this scheme. It is possible to Phish for other information in additions to usernames and passwords such as credit card numbers, bank account numbers, social security numbers and mothers' maiden names. Phishing presents direct risks through the use of stolen credentials and indirect risk to institutions that conduct business on line through erosion of customer confidence. The damage caused by phishing ranges from denial of access to e-mail to substantial financial loss
PHISHING TECHNIQUES
Phishers use a wide variety of techniques, with one common thread.
Link Manipulation
Most methods of Phishing use some form of technical deception designed to make a link in an e-mail appear to belong to the spoofed organization. Misspelled URLs or the use of sub domains are common tricks used by Phishers. In the following example, http://www.yourbank.example.com/ , it appears as though the URL will take you to the example section of the yourbank website; actually this URL points to the " yourbank " (i.e. Phishing) section of the example website.
An old method of spoofing used links containing the ' @ ' symbol, originally intended as a way to include a username and password. For example, http://www.google.com@members.tripod.com/ might deceive a casual observer into believing that it will open a page on www.google.com , whereas it actually directs the browser to a page on members.tripod.com , using a username of www.google.com : the page opens normally, regardless of the username supplied.
Filter Evasion
Phishers have used images instead of text to make it harder for anti-Phishing filters to detect text commonly used in Phishing e-mails.
Website Forgery
Once a victim visits the Phishing website the deception is not over. Some Phishing scams use JavaScript commands in order to alter the address bar. This is done either by placing a picture of a legitimate URL over the address bar, or by closing the original address bar and opening a new one with the legitimate URL.
Phone Phishing
Messages that claimed to be from a bank told users to dial a phone number regarding problems with their bank accounts. Once the phone number (owned by the Phishers) was dialed, prompts told users to enter their account numbers and PIN. Vishing (voice Phishing) sometimes uses fake caller-ID data to give the appearance that calls come from a trusted organization.
Google Chrome OS
Definition of Google Chrome OS
Google Chrome OS is a Linux operating system designed by Google to work exclusively with web applications. It is intended to focus on Web applications while running a fast and simple interface, based off Google's existing Chrome browser. Google announced the operating system on July 7, 2009 and made it an open source project, called Chromium OS, that November.
Unlike Chromium OS, which can be compiled from the downloaded source code, Chrome OS will only ship on specific hardware from Google's manufacturing partners. The user interface takes a minimalist approach, resembling that of the Chrome web browser. Because Google Chrome OS is aimed at users who spend most of their computer time on the Internet, the only application on the device will be a browser incorporating a media player.
Google Chrome OS is initially intended for secondary devices like netbooks, not as a user's primary PC, and will run on hardware incorporating an x86 or ARM-based processor. Chrome OS as a "hardened" operating system featuring auto-updating and sandbox features that will reduce malware exposure. Google claimed that Chrome OS would be the most secure consumer operating system due in part to a verified boot capability, in which the initial boot code, stored in read-only memory, checks for system compromises
Unlike Chromium OS, which can be compiled from the downloaded source code, Chrome OS will only ship on specific hardware from Google's manufacturing partners. The user interface takes a minimalist approach, resembling that of the Chrome web browser. Because Google Chrome OS is aimed at users who spend most of their computer time on the Internet, the only application on the device will be a browser incorporating a media player.
Google Chrome OS is initially intended for secondary devices like netbooks, not as a user's primary PC, and will run on hardware incorporating an x86 or ARM-based processor. Chrome OS as a "hardened" operating system featuring auto-updating and sandbox features that will reduce malware exposure. Google claimed that Chrome OS would be the most secure consumer operating system due in part to a verified boot capability, in which the initial boot code, stored in read-only memory, checks for system compromises
Introduction of Google Chrome OS
Speed is an unsaid feature of the Google Chrome OS. With Google Chrome's tremendous booting speed and more, users have a lot to say about experiencing 'waitlessness'. Waitlessness, in Google's terms, means never having to wait for the web.
Chrome notebooks boot in about 10 seconds and resume from sleep instantly. Websites load quickly and run smoothly, with full support for the latest web standards and Adobe Flash. The web evolves rapidly. Your Chrome notebook evolves with it. Every time you turn it on, it upgrades itself with the latest features and fixes. Annoying update prompts not included.
The portion of the operating system needed to operate the device will reside in a read-only section of memory. The rest of the operating system is integrated with the Chrome browser and, like the browser, security updates require nothing more than a reboot. Chrome OS can run multiple Web applications in multiple tabs and each one is locked down from all others, so vulnerability in one Web app can't lead to exposure in another
Chrome notebooks boot in about 10 seconds and resume from sleep instantly. Websites load quickly and run smoothly, with full support for the latest web standards and Adobe Flash. The web evolves rapidly. Your Chrome notebook evolves with it. Every time you turn it on, it upgrades itself with the latest features and fixes. Annoying update prompts not included.
The portion of the operating system needed to operate the device will reside in a read-only section of memory. The rest of the operating system is integrated with the Chrome browser and, like the browser, security updates require nothing more than a reboot. Chrome OS can run multiple Web applications in multiple tabs and each one is locked down from all others, so vulnerability in one Web app can't lead to exposure in another
Use of Cloud:
Users of devices running Chrome will have to perform all their computing online or "in the cloud," without downloading traditional software applications like iTunes and Microsoft Office, or storing files on hard drives. Devices running Chrome will receive continuous software updates, providing added security, and most user data will reside on Google's servers.
User data stored on the device, which is minimal, is encrypted. User data is limited to items such as user preferences. All other data will be stored in the cloud. User preferences will also be synched to a cloud account, so like any thin client. should you lose the device, you would merely log in from another one and your data and preferences should be there.
Google's Chrome OS, is designed to be a very fast, lightweight flavor of Linux that will be available on some netbooks and other PCs by the end of the year. Google hopes to achieve this small footprint and high performance by shipping an OS with only one installed program - their own Chrome browser. Users would work, live, and save things online, using Google's own cloud computing services and other similar utilities, like Microsoft's Office Web Apps . This is of course a shift from today's computing environment, where most programs are installed locally on the computer's hard drive
Design goals for Google Chrome OS's user interface include using minimal screen space by combining applications and standard Web pages into a single tab strip, rather than separating the two. Designers are considering a reduced window management scheme that would operate only in full-screen mode.
Secondary tasks would be handled with "panels": floating windows that dock to the bottom of the screen for tasks like chat and music players. Split screens are also under consideration for viewing two pieces of content side-by-side. Google Chrome OS will follow the Chrome browser's practice of leveraging HTML5 's offline modes, background processing, and notifications. Designers propose using search and pinned tabs as a way to quickly locate and access applications
User data stored on the device, which is minimal, is encrypted. User data is limited to items such as user preferences. All other data will be stored in the cloud. User preferences will also be synched to a cloud account, so like any thin client. should you lose the device, you would merely log in from another one and your data and preferences should be there.
Google's Chrome OS, is designed to be a very fast, lightweight flavor of Linux that will be available on some netbooks and other PCs by the end of the year. Google hopes to achieve this small footprint and high performance by shipping an OS with only one installed program - their own Chrome browser. Users would work, live, and save things online, using Google's own cloud computing services and other similar utilities, like Microsoft's Office Web Apps . This is of course a shift from today's computing environment, where most programs are installed locally on the computer's hard drive
Design goals for Google Chrome OS's user interface include using minimal screen space by combining applications and standard Web pages into a single tab strip, rather than separating the two. Designers are considering a reduced window management scheme that would operate only in full-screen mode.
Secondary tasks would be handled with "panels": floating windows that dock to the bottom of the screen for tasks like chat and music players. Split screens are also under consideration for viewing two pieces of content side-by-side. Google Chrome OS will follow the Chrome browser's practice of leveraging HTML5 's offline modes, background processing, and notifications. Designers propose using search and pinned tabs as a way to quickly locate and access applications
Subscribe to:
Comments (Atom)